
Kerberos 101
First of all in this blog we will discuss an authentication protocol called Kerberos. what is Kerberos? How does it work? Authentication flow How can …
Hello friends, I will make a new series about IOT Hacking because I want to share my knowledge with y’all, I hope it will be useful and easy to understand.
simply it is like a brain of devices, firmware is a piece of software that embedded into hardware, without firmware most of electronic devices wouldn’t work, it’s just an iron piece, all smart devices has its own firmware like : TVs, Cars, Smart Plugs.
I will discuss all of these in the next blog posts.
bootloader is a code that execute before operating system starts and when you want to load a new firmware into device manually we need UART,SPI communication ports and bootloader help us to interact with devices.
kernel is the central module if an operating system, that connects system hardware to application software, it also responsible for process and memory management.
it contains all files that stored for the embedded device runtime, all web servers and network files
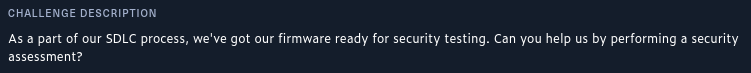
I used HTB challenge called The Needle, and this is the description of the challenge.
I use command file to detect file type
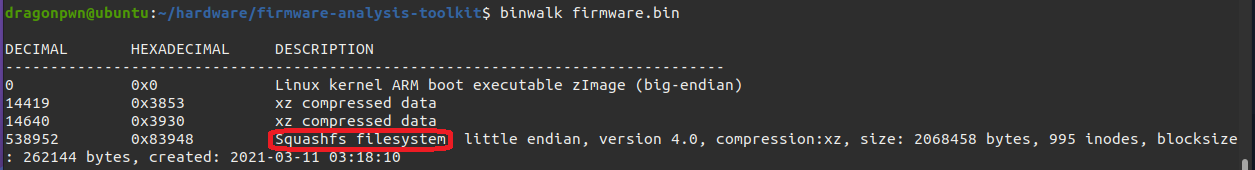
There are many types of file system like : SquashFS, CramFS, JFFS2, YAFFS2, EXT2. and the most common file system is SquashFS. and to detect the firmware file system you can use hexdump and search for magic byte or you can use binwalk, So its a Squashfs file system.
you can extract file system using Squashfs-tool or binwalk, I prefer to use binwalk.
binwalk -e firmware.bin
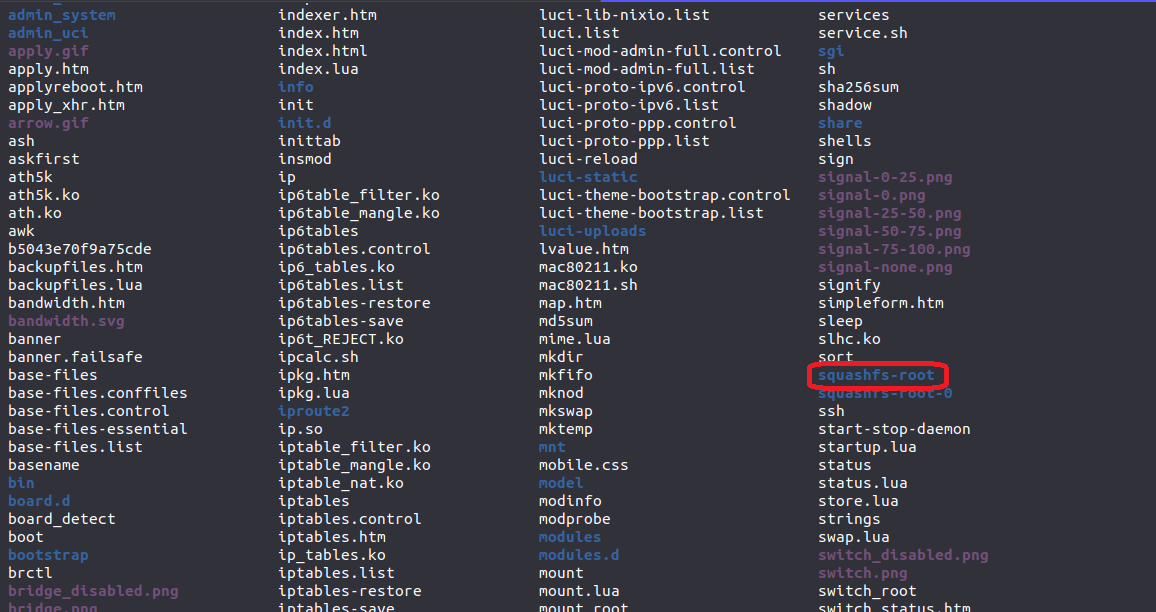
You will find file system into squashfs-root directory
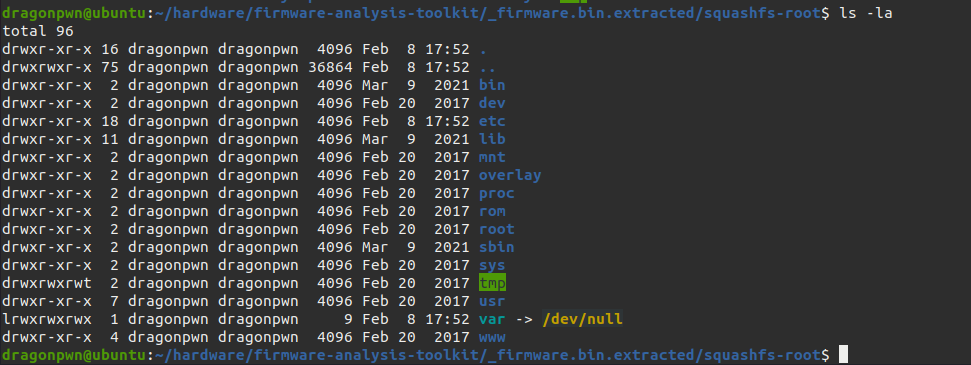
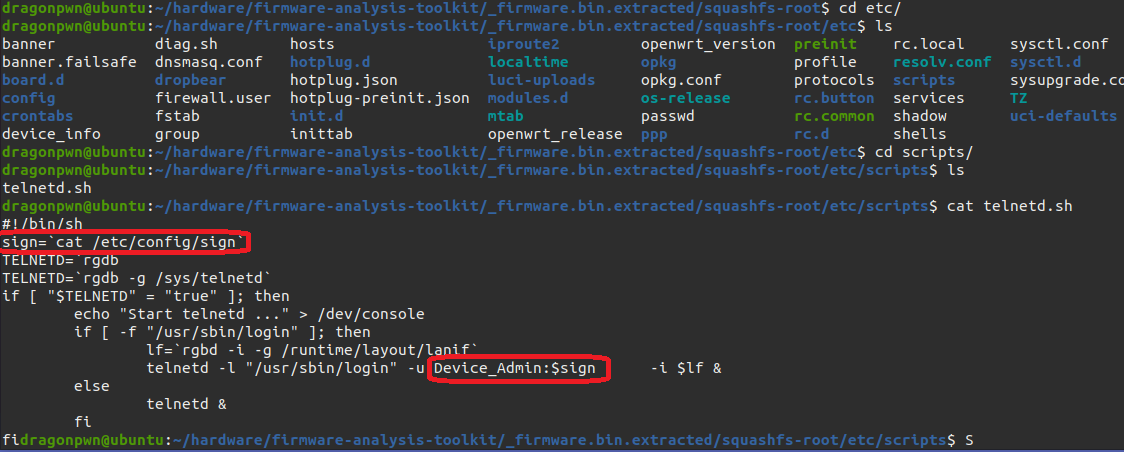
Then we need to search for telnet creds and we will find it inro etc/scripts directory
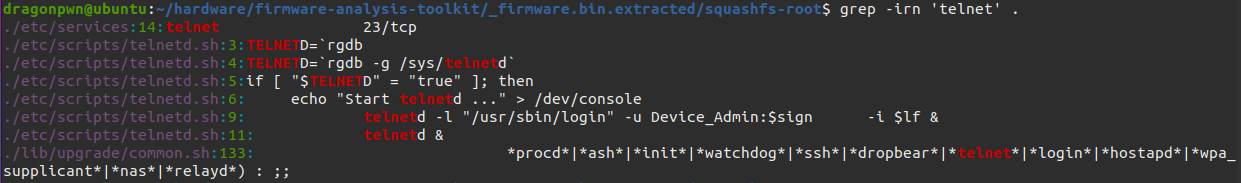
or simply you can use grep for this
as we see in telnetd.sh the user is Device_Admin and the password stored in /etc/config/sign
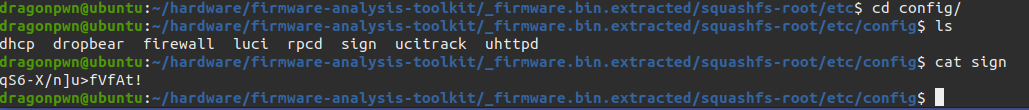
so let’s hit this creds
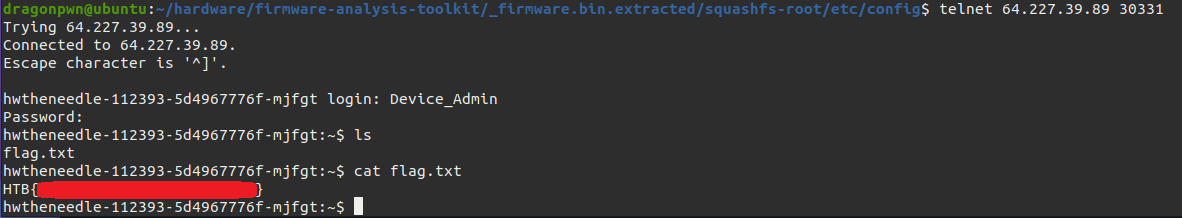
easy..peasy we got the flag

First of all in this blog we will discuss an authentication protocol called Kerberos. what is Kerberos? How does it work? Authentication flow How can …

First of all to understand the vulnerability we should reverse it. This blog will Answer these Questions 1- What is log4j 2- LDAP 3- JNDI 4- How …